Journey to the West: China SCCs and the Transfer Impact Assessment (PIPIA)
As of 1st June 2023, data exports from China can (in some cases) be facilitated using SCCs and PIPIAs (Chinese TIAs). Lucid Privacy Group provides the details and a PIPIA template.

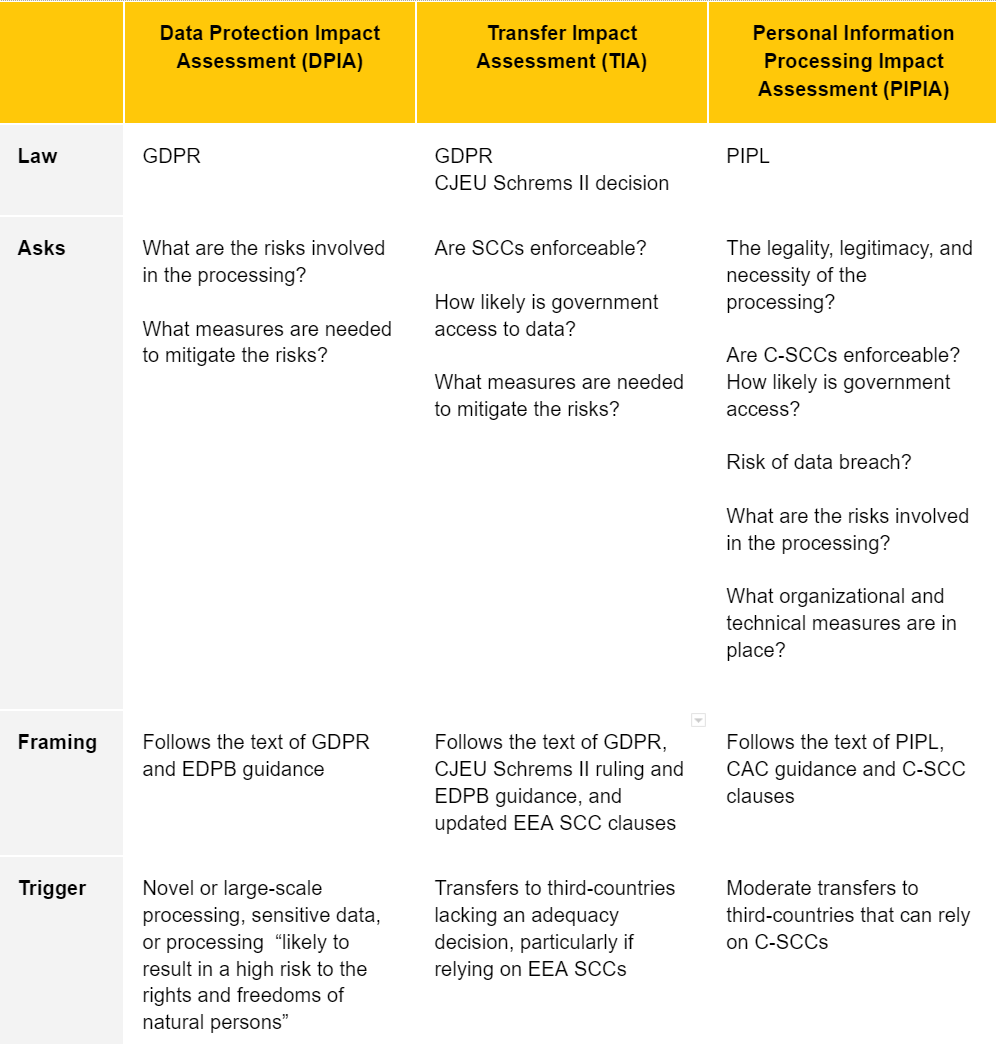
In Europe, Standard Contractual Clauses (EEA SCCs) and Transfer Impact Assessments (TIA) have become so central to organizational privacy operations that the acronyms barely need explaining.
Organizations doing business in China will therefore likely welcome the fact that as of 1st June 2023, data exports from China can (in some cases) be facilitated in a very similar fashion. Although they may not appreciate adding more letters to their growing alphabet soup of data transfer adequacy instruments.
The Personal Information Protection Impact Assessment (PIPIA) and the China Standard Contracts form the basis of China’s updated transfer mechanism largely meant for small and medium-sized businesses who process moderate amounts of data offshore.
Despite conceptual similarities, China’s approach does not carbon-copy Europe’s. With all due sympathies for our collective Privacy Acronym Fatigue Syndrome (PAFS), we need to make room for “C-SCCs” and “PIPIAs” moving forward.
Born from familiar stone
It took many years (and a few high profile court cases at CJEU) for European regulators to coalesce around exactly what a Transfer Impact Assessment is, how it works, and how it interfaces with the EU/EEA SCCs. Even with guidelines from the EDPB and rulings from individual supervisory authorities, there is still yet a definite, clear consensus around some aspects of the EU TIA process.
The position in China currently is far less clear -- understandable, given that the C-SCCs are only just coming into force.

Nevertheless, we must press on and make the best of the two official resources available to us:
- Article 5 of the CAC Measures for Standard Contracts for Exporting Personal Information Abroad, which provides, at a very high level, the requirements of a data export PIPIA.
- Article 55 of the PIPL, which provides the legal requirements for conducting a PIPIA under the PIPL.
There is clear conceptual ground cut from European bedrock, and an understanding that China is unlikely to deviate too far from compliance mechanisms both domestic and foreign multinationals need to implement. So despite trepidation surrounding the purpose and shape of a PIPIA pending further public guidance (or even discrete feedback to C-SCC applicants) the contours are well understood. It is also clear that a PIPIA is a flexible amalgam of familiar impact assessment tools.
Model behavior
Effective since November 1, 2021, the Personal Information Protection Law (PIPL) is a comprehensive personal data protection legislation. PIPL was adopted as part of a series of populist reforms that respond to Europe’s lead on global privacy matters on the one hand, and bolster China’s national security and tech policies on the other.
The PIPL is, in broad terms, modeled after the EU GDPR. However, like other such inspired frameworks it deviates from the European template in a number of important ways. Data transfers outside of China are one such example.

As in Europe, Chinese organizations have more than one data transfer mechanism available to them. These are:
- Regulatory audit. Must pass a formal security assessment by the Cyberspace Administration of China (CAC).
- Chinese BCRs. Can obtain a personal information protection certification issued by a specialized institution (sort of Chinese BCRs)
- C-SCCs. Exporters can enter into normalized contractual agreements with foreign data importers, who are in turn responsible for pushing restrictions to downstream recipients. (e.g. sub-processors)
C-SCCs can only be used by qualifying organizations, namely those that fall below the full-blown attention of the CAC:
- Not a national security interest. Organizations that are not a public utility, cloud service provider, internet service provider, telecom or other such pipeline operator.
- Moderate scale. Organization processes the PI of <1M individuals.
- Moderate transfers. Organization transfers the PI of <100K individuals annually
- Low sensitive data transfers. Organization transfers the SPI of <10K individuals annually.
‘Heaven’s Equal’ or ‘Equal Under Heaven’?
In general terms not relating to data transfers, a PIPIA is analogous to a DPIA, triggered in much the same way as an EU DPIA. However, the same term is also used in the specific context of data transfers. This suggests that the data transfer PIPIA is broader in scope than its EU TIA cousin in the same way that C-SCCs are broader (and not modular) like EEA SCCs.

Whilst the EU TIA focuses strongly (almost entirely in fact) on the nature of the recipient jurisdiction (enforceability of the SCCs and government access to data), the PIPIA goes well beyond, assessing:
- Lawfulness. The legality, legitimacy, and necessity of the purpose, scope, and method of processing personal information by the personal information processor and the overseas recipient;
- Scope. The scale, scope, type, and sensitivity of the personal information exported abroad, and the risks that the export of personal information may bring to the rights and interests of personal information;
- Efficacy. Whether the overseas receiving party has promised to undertake the obligations, and whether the management and technical measures and capabilities to fulfill the obligations can guarantee the security of outgoing personal information;
- Risks and Impacts. The risk of personal information, especially sensitive data, being tampered with, destroyed, leaked, lost, or illegally used after leaving the country, and whether there are pathways for protecting the rights and interests of Chinese data subjects;
- Governmental Policy. The impact of the national defense, foreign surveillance and counterbalancing personal information protection and redress policies of the country or region of the data importer.
- Other jurisdictional and practical matters that may affect the safe and accountable handling of personal information abroad.
Like under the GDPR and EDPB guidance, the PIPIA’s overarching concern is whether the importer can comply with C-SCCs. Unlike a TIA, which largely concerns the likelihood of a government requesting or forcing access to imported data, the PIPIA seems to ask why data should be transferred at all. We can speculate CAC is being more cautious (and protectionist) in its formulations, not only because C-SCCs are yet untried and untested, but possibly also in deference to China’s data localization requirements.
Strong traveling companions
EU TIAs ultimately revolve around the decision to put in place supplementary measures that may reduce the likelihood of governmental access (e.g. making the data less interesting). In contrast, PIPIA focuses on measures that mitigate the risk of a data breach. This is covered in more straightforward terms within the PIPIA itself and likely arises from the (ironic) knowledge that it’s not if but when data will be accessed by intelligence agencies. I.e. The US’s National Intelligence Agency as opposed to China’s own Ministry of State Security.

As such, the PIPIA seeks to understand both standard and any additional safeguards exporters and importers have implemented.
Before beginning the journey
PIPIAs must be filed with the CAC along with other accompanying documentation, which include the completed C-SCCs and a security self-assessment. Whether these will actually ever be reviewed is again an unknown, but it is important to emphasize that PIPIAs are more than internal self assessment and accountability documents. They are binding promises subject to possible surprise inspections and, yes, sanctions.

In many ways both familiar and possibly not, a PIPIA is still an accountability instrument first and foremost. There is no avoiding the fact that any organization submitting to the CAC’s procedures, such as they may be, will find itself in the palm of their hand.
Since the CAC may take sight of the PIPIA, it is currently advisable to complete PIPIAs as accurately and comprehensively as possible. At this early stage, teachings from European DPIAs and TIAs are invaluable. After all, there is only so much businesses can do to document geopolitical factors, qualify the need for offshore processing, and mitigate the risk of unbounded governmental requests short of not transferring data at all.
References
- https://www.engage.hoganlovells.com/knowledgeservices/news/key-questions-answered-chinas-regulation-of-international-data-transfers-effective-1-september-2022
- https://www.jdsupra.com/legalnews/china-s-standard-contractual-clauses-6191122/
- https://www.linklaters.com/en/insights/blogs/digilinks/2023/january/china---at-a-glance-summary-of-the-new-data-transfer-regime

